Overview
Nowadays, both governments and enterprises aim for more intelligent, automated, and efficient output with the introduction of new technology, yet there are the inevitable cyber threats. In most cases, the loss incurred by cyber attacks are associated with money, business interruption, or dwindling enterprise competitiveness. Take the common distributed denial of service (DDoS) attack for example, it could shut down e-commerce site. The 2017 terrifying ransomware WannaCry could maliciously encrypt and shut down production line, requesting enterprise to pay ransom. Hackers steal trade secrets or intellectual property, resulting in the dwindling enterprise competitiveness. What’s more, the cybersecurity vulnerabilities could also threaten public safety; imagine if critical infrastructure, such as Internet-connected medical equipment, drone, autonomous vehicle being attacked, not only money or competitiveness would be compromised, but also personal safety.
CHT Security’s team of experts has years of experience and holds hundreds of international cybersecurity certifications. The OT (Operational Technology) cybersecurity services we offer are based on IEC 62443 standards, assisting enterprise in enhancing the visibility of ICS environment, performing risk assessment, improvement actions, OT segmentation, and perimeter control. Customized network behavioral baseline, 24/7 continuous monitoring and alert, threat detection and response are also included.
OT Cyber Security Evaluation
One of the OT security services CHT Security offer is OT Cyber Security Evaluation. It provides visibility to ICS environment (including asset, network topology, and Purdue modeling, etc.), network security risk assessment and security enhancement of production line system and component, and a comprehensive testing and analysis of asset, network, and overall infrastructure in the ICS environment.
The environment will be protected prior to, during, and post the cyber attacks by implementing this service:
- Create asset inventory and network topology to enhance the visibility of ICS environment.
- Establish ICS environment cybersecurity baseline to identify abnormal network activities and to detect the intrusion of unknown asset, achieving effective protection and monitoring. Our service will also provide recommendations on network security enhancement.
- Perform potential threat and risk assessment on known weaknesses and prioritize recommended actions according to threat severity.
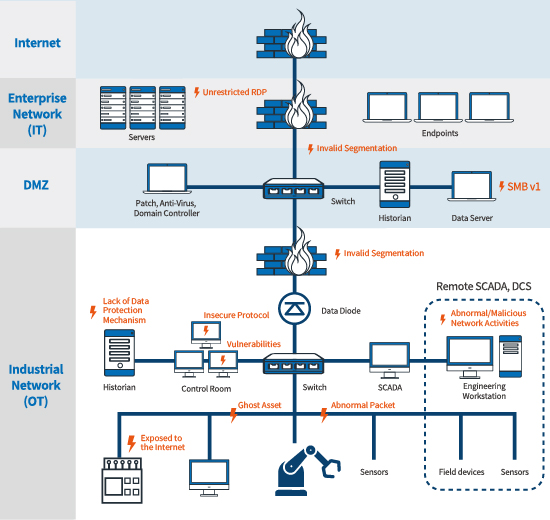
By implementing this service before attacks, the environment owner could better understand Internet-connected assets and models in the environment and obtain network behavioral baseline to detect abnormal network activities (e.g., addition of ghost assets, adoption of insecure protocols). Moreover, the owner could understand the security level of existing network and develop improvement actions through risk assessment.
OT Cyber Security Evaluation includes the following action items:
- Asset identification: asset inventory, network architecture inspection.
- Internet behavior analysis and malicious activity inspection: packet sniffing and deep packet inspection (DPI), and establishment of network behavioral baseline for OT environment.
- Risk assessment and recommended measures: weakness analysis, threat modeling, threat assessment, and recommendations.
CHT Security has performed OT cyber security evaluation for several high-tech manufactures and critical infrastructure companies in Taiwan. With the industrial threat detection system, our ICS environment network security experts could, in a timely manner, precisely discover the severity that expands the scope of the network security threat in the ICS environment.
After in-depth analysis, one of the major findings of a local high-tech manufacturer being intruded by ransomware is that its OT and IT environment were not segmented. Malware could laterally move from the compromised IT equipment to OT network and pose further threats to the essential assets of the production line. Moreover, after analysis of the Internet behavior in a CI environment, multiple essential assets in the industrial control system (ICS) were found to be exposed to the Internet, some even adopted insecure protocol.
With CHT Security’s OT Cyber Security Evaluation service, the asset, Internet connection, and overall infrastructure in the ICS environment will be overviewed, protocol security inspected, network behavior analysis and risk assessment performed, recommendations provided to the environment owner, to enhance the environment’s security.
OT SOC Monitoring Service
With CHT Security’s OT SOC monitoring service, potential cyber threats will be analyzed, real-time cyber incident alert provided, cybersecurity threat landscape effectively informed, OT environment cybersecurity enhanced, and the stability, accuracy, and effectiveness of the ICS ensured.
The benefits of OT SOC monitoring service are listed below:
- Establish customized correlation rules for OT environment based on anomalies, major changes, and malicious activities, and execute 24/7 monitoring and alert.
- Detect attack traffic, malicious activities, and impact scope could be analyzed and alert could be generated through OT continuous threat detection system, decrease incident response time.
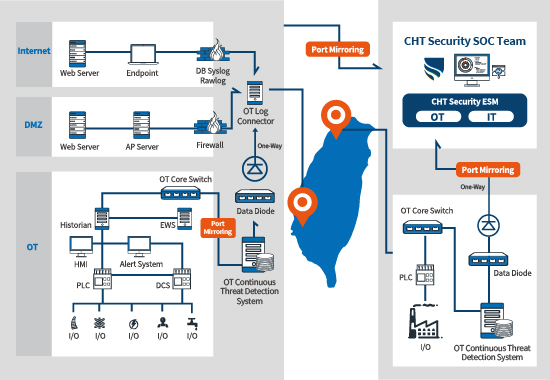
The implementation process of OT SOC Monitoring Service briefly stated below.
- Determine an appropriate interface for OT mirror port.
- Implement OT continuous threat detection system.
- Implement data diode.
- OT continuous threat detection system log integrated into the log connector in OT environment.
- OT equipment (e.g. PLC) log integrated into the log connector in OT environment.
CHT Security has provided SOC service to a domestic logistics company and assisted a CI company to develop OT SOC implementation. After considering the characteristics of the environment, we would plan the log collection mechanism of OT equipment and industrial threat detection system. With the support from our ICS environment network security experts, industrial threat detection equipment and network security joint defense process, 24/7 real-time monitoring, analysis, and cyber threat alerts of the industrial network area will be executed to protect important assets and the availability of the ICS, and to rapidly aggregate the threat impact.
Target Clients
OT Security services is suitable for industries such as manufacturing, industrial process control, smart buildings, critical infrastructure (CI), railway system, electric power, healthcare.
Video
More testing services:
- Red Teaming please click here
- Penetration Testing please click here
- Vulnerability Assessment please click here
- Social Engineering Assessment please click here
- Mobile App Security Assessment please click here
- Source Code Security Analysis please click here
- Cyber Security Evaluation please click here
- IoT Testing please click here
- OT Security please click here
