Overview
This service consists of Network Architecture Review, Network Traffic Analysis, Server Inspection, Configuration Review and PC Inspection. We provide enhancement recommendations through the integrated security assessments.
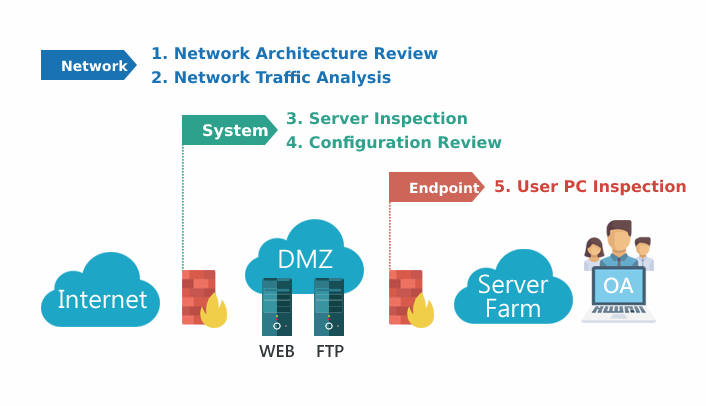
Check Items
Check Item | Description | |
Network Architecture Review |
| |
Network Traffic Analysis | Packet capture and analysis |
|
Network device log analysis |
| |
User PC Inspection | User PC malware inspection |
|
User PC update check |
| |
User PC configuration review |
| |
Server Inspection | Server malware inspection |
|
Server update check |
| |
Configuration Review | Review policies of directory servers |
|
Firewall policy review |
| |
Features
Our self-developed 5-in-1 Cyber Security Evaluation platform consist of malware detection, OS update check, configuration check, database update check and 3rd party software update check.
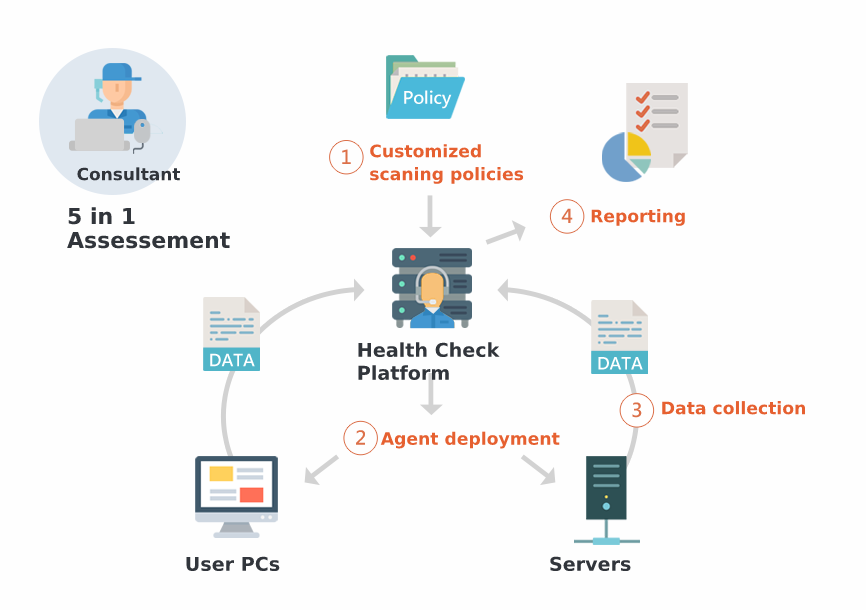
Target Clients
Cyber Security Evaluation is mainly for government agencies, educational institutions, state-owned business, medical institutions and enterprises.
Goal
Cyber Security Evaluation is to assess the overall security strength from the aspect of network, system and endpoint. Through identifying the weakness in architecture and providing recommendations, we deliver references for security enhancement.
The benefits are as follows.
- Combining with automated tools and expert inspection, we can spot malwares and suspicious files in your servers, then we analyze and eliminate them.
- Through network traffic analysis and inspection, we can find out malicious connections from/to infected servers. Then we monitor and protect them and provide enhancement recommendations.
- Through interviewing server/equipment administrators and scanning with professional tools, we can identify the risks in server configuration, firewall planning and network architecture then harden the protection.
Award
In the “Review of the Security Service Provider” by Security Department of the Executive Yuan, CHT Security is the only security company that has achieved the top-notch grade in SOC, cyber security evaluation, penetration test and social engineering assessment for consecutive years.

More testing services:
- Red Teaming please click here
- Penetration Testing please click here
- Vulnerability Assessment please click here
- Social Engineering Assessment please click here
- Mobile App Security Assessment please click here
- Source Code Security Analysis please click here
- Cyber Security Evaluation please click here
- IoT Testing please click here
- OT Security please click here
