Overview
The Source Code Analysis service can quickly analyze your source code for vulnerabilities, identifying potential risks of the system. By supporting developers to fix the source code, the security of the system can be effectively improved. With the precise fixing of system vulnerability, the cost excessive developers’ effort can also be reduced.
Benefit
The Source Code Analysis analyzes program vulnerability of the target system in a static way. The benefits of static analysis are:
- A Complete Analysis: 100% source code coverage, ensuring that all program execution paths are effectively analyzed.
- A Clear Result: Clearly indicates the locations of vulnerabilities and the paths of vulnerabilities. This can lead to the most effective fixing.
- Impact Free: without an attack, there is no impact on the production system. This prevents any effect to the customer in the analysis process.
Advantages
- A Trustworthy Service Provider: Source code is a critical intellectual property for software vendors. Our team will protect the sensitive information with the highest care for all customers. If necessary, we provide on-site analysis to avoid exporting your source code from your organization.
- A Professional Team: Our team has practical experience in both security testing and security development. From a developer’s point of view, we can provide the most effective fixing recommendations. This avoids the low development efficiency caused by irrelevant security requirements.
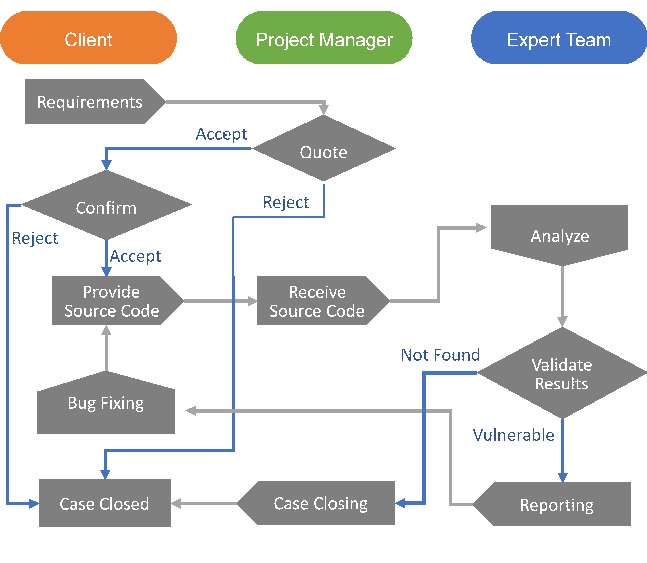
Service Flow
Analysis Tool
This service performs analysis with Micro Focus Fortify SCA. Fortify SCA has the following features:
- A Market Leading Brand: It has been listed as “Leader” in Gartner Magic Quadrant for years. Thus, the analysis reports also share the same credibility.
- Support a wide range of languages: common languages for web/mobile applications such as .NET, Java, PHP, Java (Android), Objective C are supported and followed with continuous updates.
- Comply with international standards: with a mapping to international standards, such as OWASP Top 10, OWASP Mobile Top 10 and SANS Top 25, developers can quickly understand the test results.
More testing services:
- Red Teaming please click here
- Penetration Testing please click here
- Vulnerability Assessment please click here
- Social Engineering Assessment please click here
- Mobile App Security Assessment please click here
- Source Code Security Analysis please click here
- Cyber Security Evaluation please click here
- IoT Testing please click here
- OT Security please click here
