Overview
With the rise of smart applications like IoT (Internet of Things), a great amount of traditional equipment, from TV, lightbulb to medical and industrial equipment, are now able to connect to the Internet. However, the accompanying risks are also on the rise. More and more cyber attacks on IoT device take place every day. A negligible IP Cam or printer being intruded could leave a backdoor for hackers to access internal network, resulting in extremely high risk for enterprises. It could even lead to social paralysis or death.
Threats specific to IoT devices are as shown below:
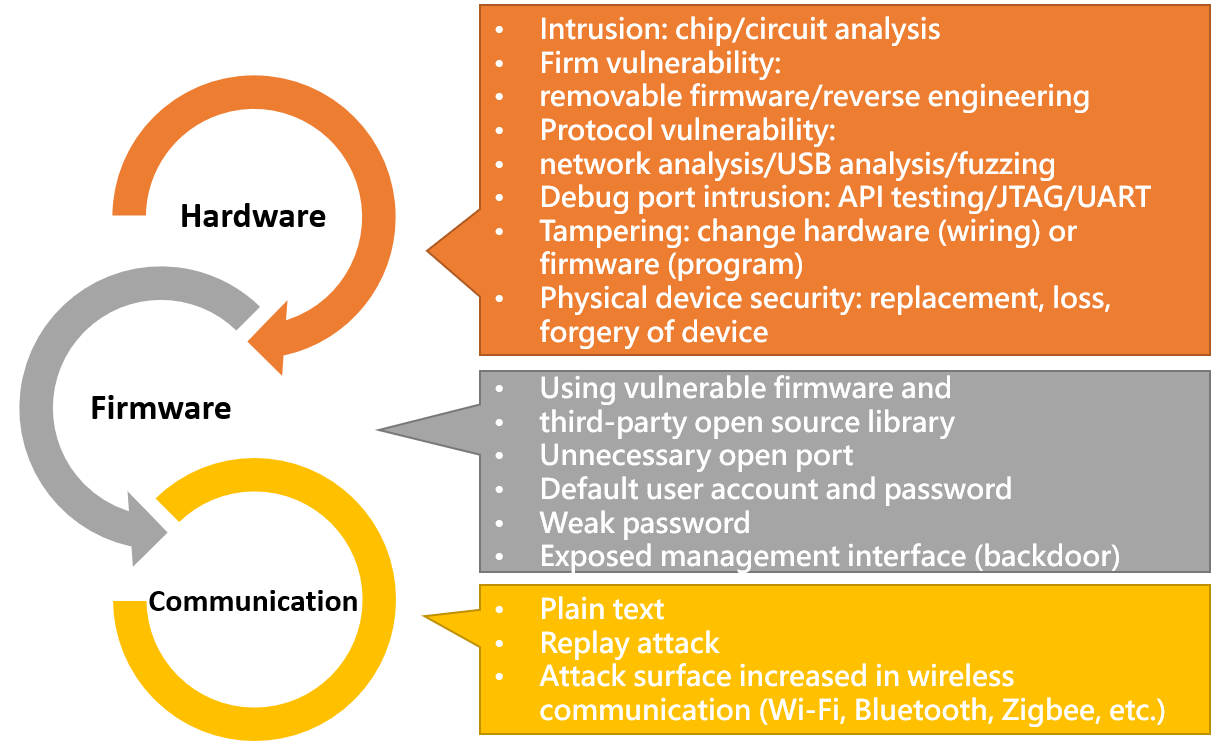
IoT testing takes references from sources of threat and OWASP IoT Top 10 common vulnerabilities when implementing testing on different layers, including hardware, firmware, communication (wireless communication interface included), to simulate cyber attacks. By attempting to identify every type of intrusion, it is possible to patch vulnerabilities ahead of time to protect network security.
Features & Advantages
- 2018 Champion of International Bug Bounty Challenge held by ITRI.
- 2018 Champion of HITCON Defense Contest.
- 2019 Second Place Winner of 2019 Red Alert 72 Contest by TWCSA.
- Receiving straight A’s/Excellence (i.e. 1st place) in Penetration Testing in “Review of the Security Service Provider” by Security Department of Executive Yuan, Taiwan for consecutive years.
- Team members with CEH, ECSA, GWAPT, GPEN, CISSP, OSCP. OSED. CREST... certifications and years of experiences in inspection.
- Capabilities of discovering 0-Day vulnerabilities in servers, websites, mobile apps, applications, IoT devices, etc.
- Team with experiences in both attacking and defense to assist enterprises in achieving the utmost security.
- Team certified by ISO 20000 to guarantee service quality and project execution.
- Protecting enterprise’s confidential data with our trustworthy brand and outstanding experts executing stable testing services.
- Delivering effective total solutions to satisfy all your needs.
Target Customers
- Smart manufacturing
- Smart healthcare
- Smart housing/buildings/cities
- IoT Application in Critical Infrastructures
- V2X (Vehicle-to-everything) Application
- IoT device manufacturers
Benefits
- Ensure the security of installation settings, identity verification, and privacy protection mechanism of IoT devices.
- Enhance network robustness by preventing IoT devices from becoming the cause of network security breach.
- IoT devices fully tested prior to release for public use to reduce patching, updating and recall costs by discovering issues in advance.
Other Services
In addition to IoT testing, our team also provides services such as Secure System Development Life Cycle (SSDLC) training, IoT agent, IoT SOC, IoT honeypot and intelligence, and cyber security incident response and digital forensics.
More testing services:
- Red Teaming please click here
- Penetration Testing please click here
- Vulnerability Assessment please click here
- Social Engineering Assessment please click here
- Mobile App Security Assessment please click here
- Source Code Security Analysis please click here
- Cyber Security Evaluation please click here
- IoT Testing please click here
- OT Security please click here
