Overview
We are composed of the former members from the Chunghwa Telecom Data Division that was awarded as “Excellent” in the Executive Yuan’s Cyber Security Service Provider Review.
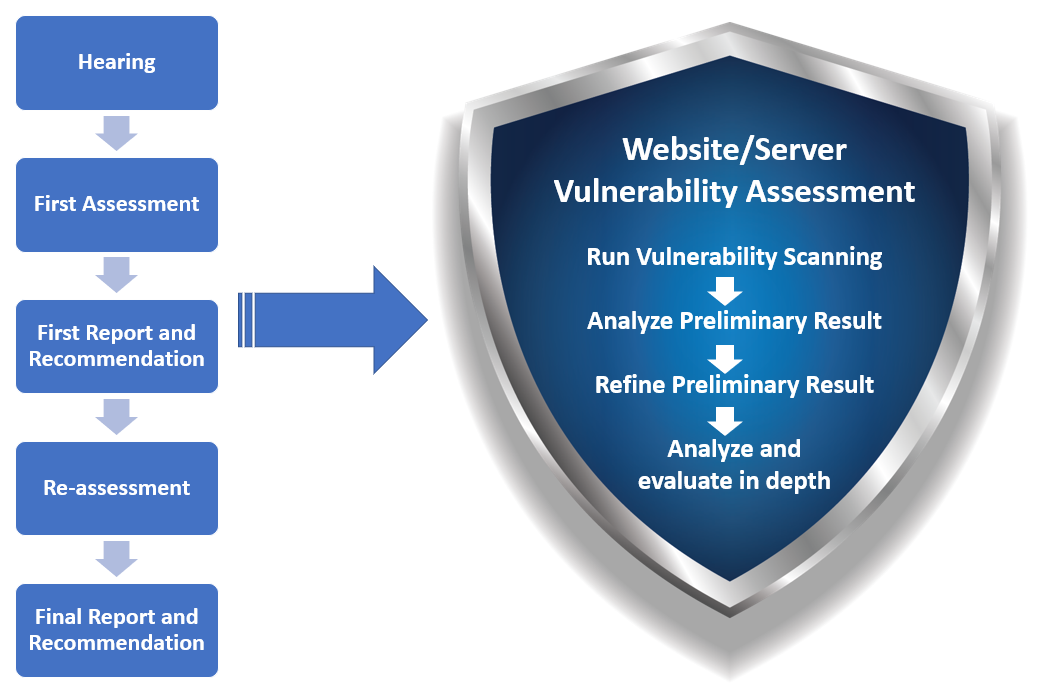
The service includes host vulnerability assessment and website vulnerability assessment depending on the characteristics of the targets. The vulnerability assessment service utilizes high-efficiency tools to perform security vulnerability scanning on the targets and look for known vulnerabilities.
Suggestions and reports will be provided with the scan results for clients to fix the vulnerabilities. A re-assessment will be provided after vulnerability fixing. A cross analysis can be done with the before and the after. With the vulnerability statistics, clients can further lower the risks of being hacked.
Benefits
- Professional analysis of the results to enhance comprehension.
- Recommendations on the fixing scheduling to quickly reduce the risk.
- Elevate the effectiveness of vulnerability fixing with the support from professional consultants.
- Reduce scanning risk with requirement interviews.
Advantages
- Adopting awarded global leading brand scanning tools.
- Combining Chunghwa Telecom vulnerability management system to track and manage vulnerabilities.
- Providing fast responses to vulnerability fixing inquiries with our self-built vulnerability fixing knowledge database.
Service Flow
Testing Tools
We utilize different tools to match your requirements:
1. For host vulnerability assessment, we adopt Tenable Nessus Professional with SecurityCenter:
(1) Rich number of vulnerability checking: covering multi operating systems, malwares and network devices with timely updates.
(2) Quantifying risks: providing intuitive scoring system based on vulnerability and importance of the assets. The result can show the recent overall risk level of the enterprise network.
2. For website vulnerability assessment, we adopt Acunetix Web Vulnerability Scanner which has good balance in scanning speed, depth, broadness:
(1) Supporting many checking items: more than 4500 checking items including SQL Injection, XSS, XXE, SSRF and Host Header Injection.
(2) Complied with multiple standards: complied with OWASP Top 10, PCI DSS and HIPAA.
More testing services:
- Red Teaming please click here
- Penetration Testing please click here
- Vulnerability Assessment please click here
- Social Engineering Assessment please click here
- Mobile App Security Assessment please click here
- Source Code Security Analysis please click here
- Cyber Security Evaluation please click here
- IoT Testing please click here
- OT Security please click here
