Overview
Red Teaming is to complement the easily overlooked perimeter defense in penetration testing and the deployment blind spots due to human error. Using the intelligence from public information, social networks, darknet and combining the knowledge, offensive and defensive skills and hacking tools from our security experts, we conduct intrusion simulation against agreed target organization by all means. This can verify the Blue Team capabilities in detection and response.
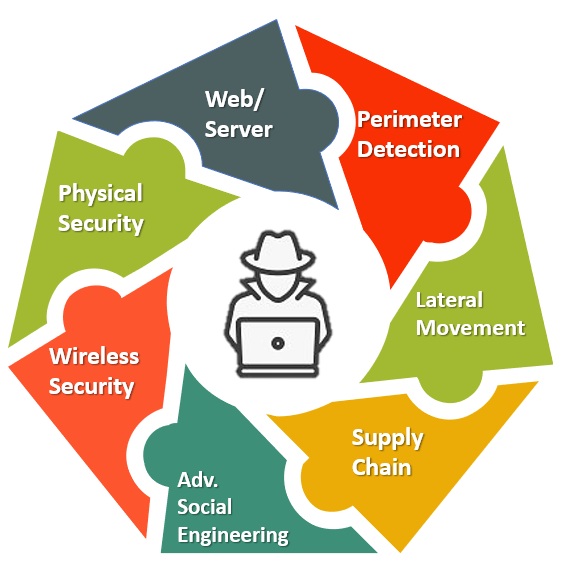
The intrusion paths in Red Teaming may consist of different methods, including but not limited to the following:
Awards & Advantages
- 2018 Championship Winner of HITCON Defense Contest, and winner of the Special Award for Intelligence Sharing.
- 2018 Championship Winner of International Bug Bounty Challenge held by ITRI.
- Runner-up of 2019 Red Alert 72 Contest.
- Top featured provider in “Review of the Security Service Provider” by Security Department of Executive Yuan, Taiwan for consecutive years.
- Experienced members with certifications of CEH, ECSA, GWAPT, GPEN, CISSP, etc.
- Capabilities in discovering zero-day vulnerabilities in servers, websites, mobile APPs, desktop applications, IoTs, etc.
- Harden the information systems for customers by the cybersecurity team specialized in both attack and defensive techniques.
- ISO 20000 ITSM and ISO 27001 ISMS to assure the service quality and project execution.
- The trustworthy brand with qualified security assessment engineers to protect business secrets from leakage.
- Provide a wide range of effective solutions to meet the needs of one-stop shopping.
- Red Teaming Service Wins 2024 Cyber Security-Pilot Award.

Target Customers
- Mature organizations that routinely conduct black/white box security assessments to discover blind spots through larger scale drills.
- Large organizations that had implemented protections and SOC to test the detection and response mechanisms through drills.
- Organizations that has a vast network boundary and wish to find out the pain points and the priorities of security investment through actual drills.
Case Study
Attacks can take place in a variety of paths from different entry points and through different network connections. Below is one example.
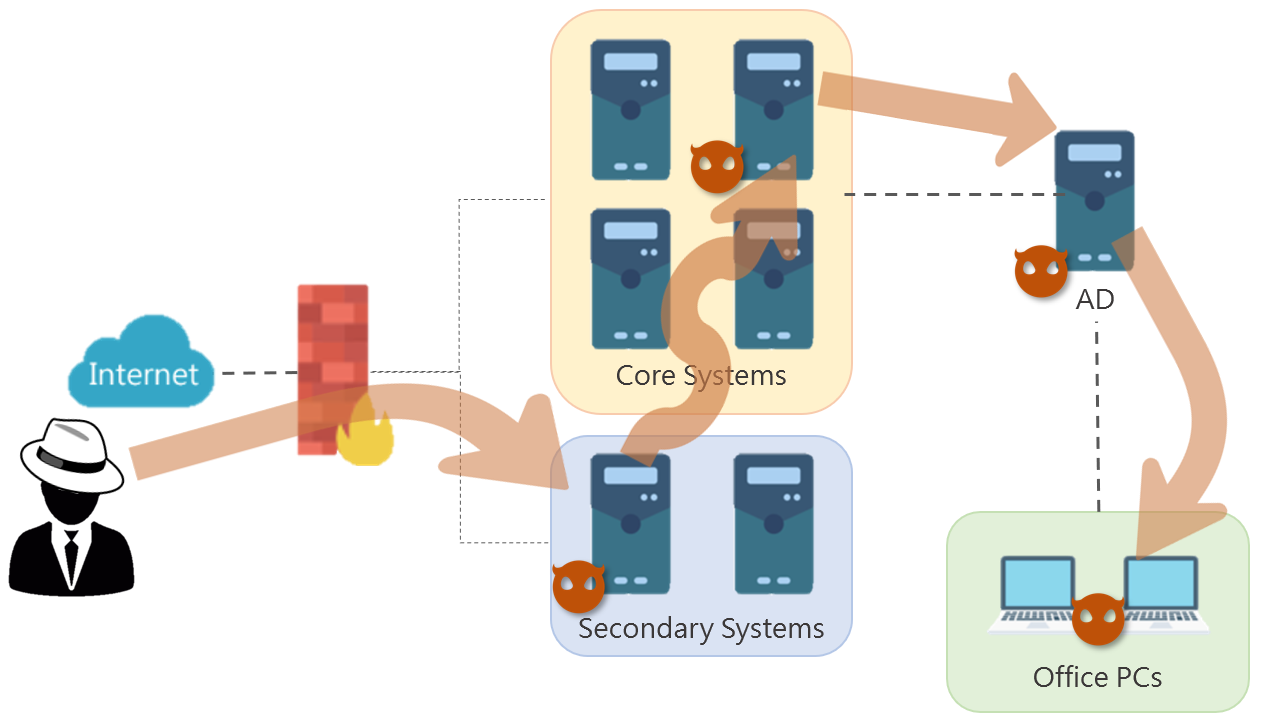
- Testers found an injection vulnerability in a secondary e-learning system and then obtained the administrator credential. Logging in as the administrator, testers abused a bulletin attachment upload vulnerability and then obtained the administrator privilege of the server.
- The secondary system was in the DMZ where core systems were also located in. By abusing the vulnerability in the internally open SMB service, testers obtained the server administrator privilege of the core system server.
- Testers enumerated existing accounts in the AD connecting to the core systems. With the DB and OS password rules obtained in the foregoing process, testers formed a special password file. With AD misconfiguration, Kerberoasting and other vulnerabilities, testers continuously tried to obtain higher privileges. As a result, testers obtained the domain administrator account.
- Then testers could deliver the malware to any host target via AD and obtain confidential information to achieve the drill goal.
- Finally, the enterprise client obtained the drill results, patching suggestions and expert consultancy for Intensifying from the inside out and greatly increasing the barrier against intrusion.
Note: In the routine penetration testing of the client, the secondary systems may only be tested once before the release, or even never be included in any assessment.
Service Comparison
Service | Item | Vulnerability Assessment | Penetration Testing | Red Teaming |
Definition | Detect vulnerability with automated tool within a specific scope | Simulate hacker intrusion within a specific scope | Full range simulated intrusion against target organization without a scope limitation | |
Qualification | Basic security skill | Certified ethical hacker | Capable of zero-day vulnerability discovery | |
Tool | Single tool | Multiple tools used for vulnerability analysis | Plus darknet intelligence, reverse connection, cracking tools, C2 servers | |
Cost | Low | Moderate | High | |
Deliverable | Vulnerability Consultancy | Yes | Yes | Yes |
Report | Vulnerability listing | Vulnerability listing with evidences | Plus collected intelligence and intrusion paths, timeline | |
Scope | Web/Server | Yes | Yes | Yes |
IoT/OT Testing | Optional | Optional | Yes | |
Boundary Detection | Yes | |||
Lateral Movement | Yes | |||
Wireless Testing | Optional | |||
Physical Security | Optional |
More testing services:
- Red Teaming please click here
- Penetration Testing please click here
- Vulnerability Assessment please click here
- Social Engineering Assessment please click here
- Mobile App Security Assessment please click here
- Source Code Security Analysis please click here
- Cyber Security Evaluation please click here
- IoT Testing please click here
- OT Security please click here
