Service Description
CHT Security’s cybersecurity threat detection management service, commonly known as the Security Operation Center (SOC) service, aims to aggregate cybersecurity information. It provides early warning threat intelligence prior to cyber incidents, real-time warning during cyber incidents, as well as post-incident threat analysis and recommendations. Our SOC service offers effective management for diverse cybersecurity alerts so our customers can better prioritize cybersecurity risks and allocate resources. Through cybersecurity monitoring, customers can understand both internal and external security threats in real time and respond to cybersecurity incidents in the first instance in order to minimize impact.
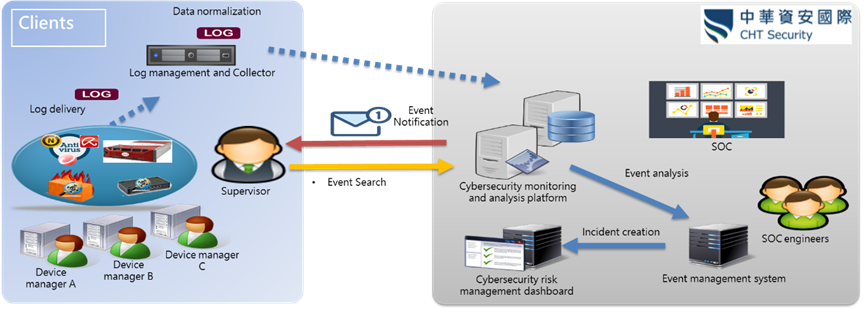
The CHT Security SOC service integrates People, Product and Process. The CHT Security team offers effective management service for security products, network equipment, user equipment and any violation of security CIA triad in the client’s organization. Furthermore, our SOC service provides 24/7 real-time monitoring, detection and response for security incidents. This service provides client-side log collectors to aggregate logs from relevant cybersecurity devices, operating systems and servers such as firewall, IDS/IPS, WAF, anti-virus and DLP. These logs are then encrypted and sent back to CHT Security for multi-dimensional data correlation analysis. When a cybersecurity incident or network connection anomaly is detected, our client will be notified by e-mail and SMS message, enabling rapid incident response. Moreover, a personalized dashboard webpage provides our customers with a complete overview of cybersecurity incidents, up-to-date cyber threat intelligence and monthly service reports.
Advantages
CHT Security utilizes its ISP resources to acquire the latest global malware and virus threat intelligence, providing in-depth analysis of new attack methods base on the Mitre ATT&CK framework. Moreover, the accumulated experience from past cyber drills and incident responses has been integrated into artificial intelligence (AI) and machine learning (ML) technology. These technologies have been utilized in several automated tools and early warning systems to further enhance CHT Security’s service capacity. The CHT Security SOC has integrated the Security Orchestration Automation Response (SOAR) mechanism, which incorporates a variety of device customization scripts (Playbook) for automated response and further enhances event inspection and verification efficiency. In addition, Managed Detection and Response (MDR) for cloud and network services is also integrated into our SOC service to improve the visibility and accuracy, which makes CHT Security the first and only cybersecurity company in Taiwan to integrate both SOC and MDR services.
CHT Security’s SOC service provides multiple threat hunting solutions in accordance with client environment and threats. Several platforms are also utilized for data analysis and overall incident process optimization. The CHT Security SOC team has developed a specialized incident tracking system which manages the incident process status in real time and provides a clear overview of incident handling status through a graphical interface. Furthermore, a complete record of incident handling and a diverse set of reports are generated to enable efficient incident reporting and faster incident tracking time. In addition to providing SOC monitoring services, CHT Security has also assisted numerous clients with establishing their SOC systems, including mechanisms such as loggers, SIEM and cybersecurity risk management (SRM) platforms.
CHT Security SOC awarded the COMPUTEX Best Choice Awards Cybersecurity Award in 2022, to acknowledge the advantages of this service.

Certifications & Awards
CHT Security cybersecurity threat detection management (SOC) service has been certified by ISO 20000 ITSM, ISO 27001 ISMS and ISO 27701 PIMS to ensure the best service management and data security are offered to clients. The CHT Security team has been recognized for its practical experience and blue team capacity, which received first place at the HITCON Defense Contest 2018. CHT Security was also recognized by NCCST as the best rated vendor (A-grade) from 2019 to 2021. In addition, CHT Security was awarded the “Cybersecurity Best Service Award” at the COMPUTEX Best Choice Awards in 2022, owing to the excellence of cybersecurity services they have provided to the customer.
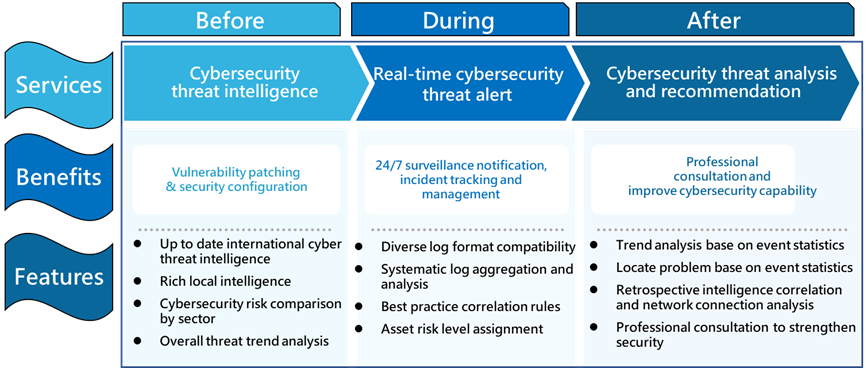
Benefits & Features
The benefits of adopting CHT Security SOC service:
- Access the latest intelligence on cybersecurity threats and intra & inter-industry threats, and implement protective measures.
- 24/7 monitoring of cybersecurity security threats and receive notification in real time.
- Establish an incident tracking mechanism to implement cybersecurity governance and have a clear overview of cybersecurity risks.
- Receive professional consultation advise and improve the cybersecurity capacity.
The main features of CHT Security SOC:
- Offers rich intelligence sources which can be utilized to prevent security threats in advance and generate accurate security alert rules.
- Systematic threat analysis is compatible with a diverse set of device logs.
- Well-established practical experience from providing services to diverse industries over the years.
- Offers big data retrospective analysis and evaluates the impact of latest cybersecurity risks proactively.
- Offers personalized web service interface for effective incident tracking and managing cybersecurity risks.
